Gozi (Ursnif) is a notorious and widely distributed banking trojan. It is so widely distributed that, according to IBM, it makes up 25% of all malicious activity targeted towards financial institutions, it is a threat that has been on the landscape for multiple years. Previous breaches have heavily targeted the healthcare sector, which led to the compromise of data associated with 3.7 million patients costing $5.55 million.
Over time attackers utilizing Gozi are continually modifying their techniques in order to avoid detection. The malware itself has featured heavily since 2007 and now after over a decade after it was first found, it as seen as the most prevalent financial malware:
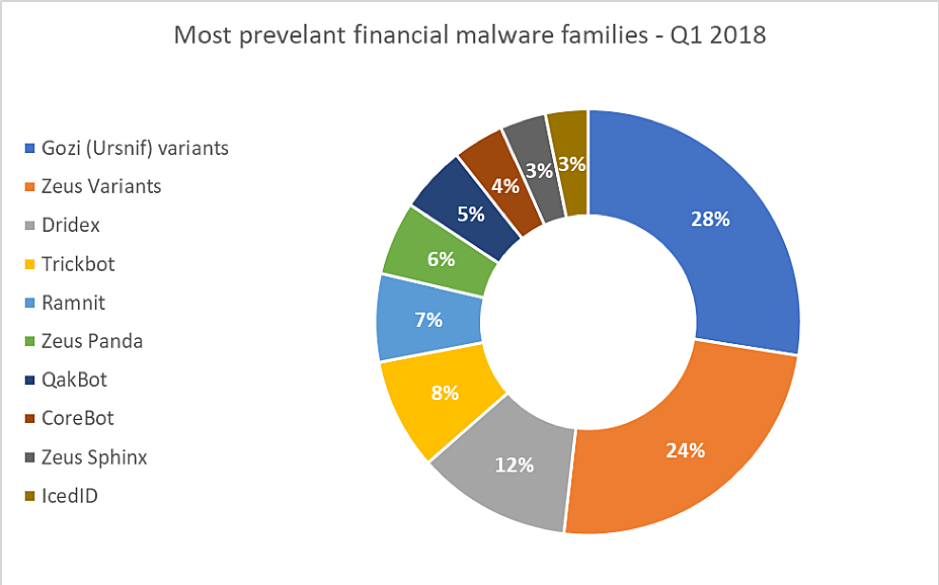

Distribution Details
Typically the threat actor distributes this malware in low-volume targeted attacks, as opposed to mass spam mail campaigns. By utilizing this tactic, they are able to stay under the radar and spend their time crafting convincing, well-executed emails and maximize the chance that the email will be opened and the packet downloaded.
The attackers move swiftly from domains and IP addresses, not only for each campaign but for each individual email, making it almost impossible to block. The campaigns themselves are launched weekly in order to dupe more victims and generate more money for attackers.


The Infection
The malware is typically distributed using malicious spam email campaigns, which feature a Microsoft Word file which acts and the payload downloader. Hackers attempt to make the email seem like it is part of an existing thread in the hopes to increase its legitimacy and open rate. The emails are usually well crafted and written – something that is not typical for most mass-email campaigns.
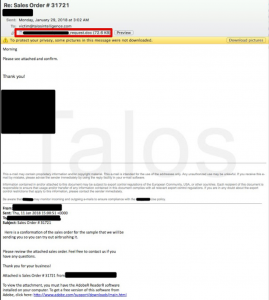

The word file comes with an embedded VBA which is executed when the word document is closed. This is smart as by only activating once the document is closed it can bypass some sandbox systems which are activated only when documents are opened.
What Does Gozi Do?
Gozi is able to inject itself into Windows operating systems web browsers, allowing hackers to monitor browsing activity and hoover up data and credentials that are put into forms.
We educate.
We update.
We protect.
We secure.
We back up.
You can learn more about Aware’s RMM solution here or contact our IT Security team.
Digital Marketing Manager at Aware Group: Working his way through the world of technology and Thailand as best as he can. Happy to contribute to other tech publications.