Spora ransomware is a sophisticated form of ransomware distributed by organised syndicates with the very special ability to work offline. It was first detected in January 2017 but has a resurgent strain.
The Spora ransomware targets all versions of Windows including Windows 10, Windows 8, and Windows 7. Although the first strain was distributed in January, a new strain has been detected which tries to conceal the virus and bypass antivirus software and email filters.
How is Spora distributed?
Spora is distributed through various ways, usually spam emails, with malicious attachments OR from phishing emails, which direct you to infected websites dropping malicious payloads. Usually, the emails are branded under the guise of a major company, notifications of shipments, or invoices are common for scammers to use and frequently opened by users leading to infection.
The initial Spora ransomware was previously distributed in a multi-stage attack, 1. The victim receives the ZIP file and is invited to look inside, 2. The zip file contains a HTML application (HTA File) with an enticing name 3. The HTA file contains a script that runs an embedded JavaScript file. In this version, scanning tools were able to notice that the HTA file contained malware, and raise alerts.
The new strain approaches detection differently, convincing the filters and antivirus software that the attachment contains a PDF file, scanners typically ignore file extensions, instead of examining the bytes contained in the file.
The new Spora strain’s initial bytes make it appear to be a PDF to email filters and virus scanners, however, it is still opened as an HTA file. This is dangerous as when opened in Windows the malicious attachment opens a webpage that isn’t subjected to the same security restrictions.
What does Spora do?
Once deployed, the Spora ransomware runs silently and encrypts files with selected extensions. Each file is encrypted with separate keys.
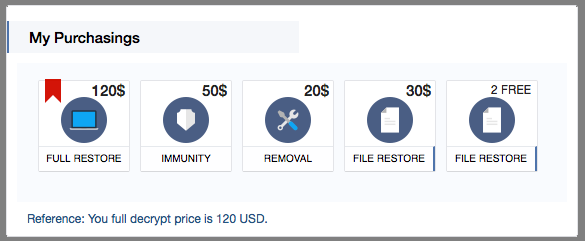
Once your computer has been infected you are linked to a website, with four payment options. In order for the attackers to advertise their “trustworthiness”, and to prove they do in fact have the decryption key they will allow you to decrypt two files for free.
From their price point, the full restore is $120 meaning you will get all your files restored. The immunity package somewhat curiously means that they will stop you getting infected again, although we haven’t tested this and it seems unlikely to be true. Removal tool, we suspect is due to more and more people backing up, they simply want the ransomware removed from their computer.
It is encouraging that removal and immunity are now becoming available as it means that users are now backing up their files.
Claim your free Ransomware protection trial here: http://bit.ly/2yffTYW
Digital Marketing Manager at Aware Group: Working his way through the world of technology and Thailand as best as he can. Happy to contribute to other tech publications.